The Ultimate Guide to Blockchain Identity Verification Tools: Secure Your Digital Identity
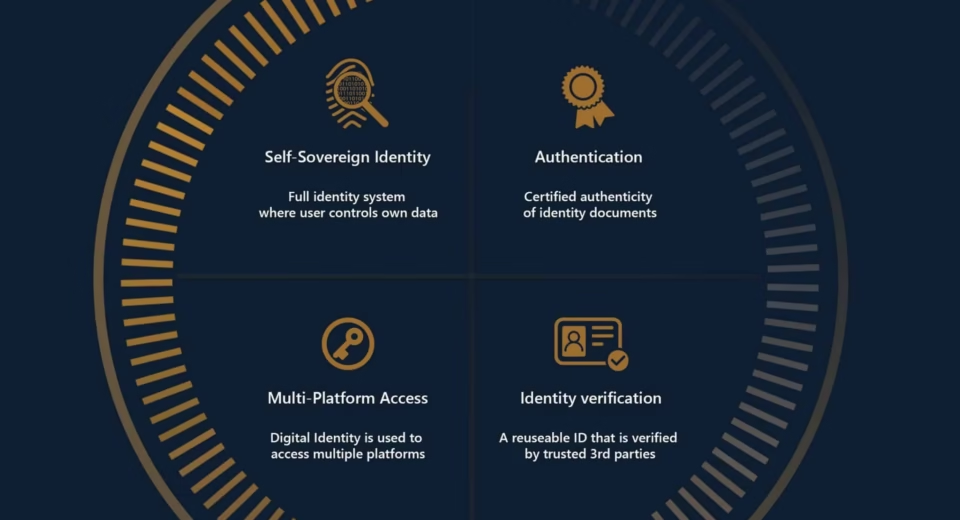
Blockchain Identity Verification Tools: The Future of Secure Digital Identity Estimated reading time: 15 minutes Key Takeaways Blockchain identity verification tools offer enhanced security through decentralization and immutability, eliminating single points of failure. Users gain privacy and control over their identity data with features like selective disclosure and self-sovereign identity. Advanced privacy tech such as […]