The AI Cybersecurity Arms Race: Securing WordPress Against Automated Exploits in 2024
Estimated reading time: 11 minutes
Key Takeaways
- The speed of AI systems means the urgency of the new security challenge facing traditional CMS platforms like WordPress is unprecedented, exploiting flaws faster than humans can react.
- **WordPress security flaws exploiting AI** refers to the automated, mass weaponization of component vulnerabilities by machine learning tools.
- *Defense must be AI-enabled.* Next-generation Web Application Firewalls (WAFs) and behavioral monitoring are now non-negotiable necessities.
- Hardening focuses on strict operational hygiene (2FA, least privilege) and continuous, automated patching.
- For maximum resilience, decoupling the presentation layer (Headless WordPress) drastically reduces the publicly exposed attack surface.
Table of contents
- The AI Cybersecurity Arms Race: Securing WordPress Against Automated Exploits in 2024
- Key Takeaways
- The New Era of Automated Threats
- How AI is Weaponizing WordPress Vulnerabilities
- Critical Security Guide for WordPress 2024: Essential Measures
- Securing the Supply Chain: The Weakest Link
- Architectural Defense: Adopting Headless WordPress
- Recommended Security Toolkit: Products and Services
- Summary and Final Checklist
- Frequently Asked Questions
The New Era of Automated Threats
The internet is changing, and so is cybersecurity. For years, WordPress has been the dominant force on the web, powering over 43% of all websites. Its accessibility is its strength, but its vast ecosystem of themes and plugins is now its greatest liability in the face of machine intelligence.
We are currently navigating an urgency of the new security challenge facing traditional CMS platforms like WordPress, where automated AI systems can scan and exploit vulnerabilities *orders of magnitude* faster than human defenders can identify, test, and patch them. This is not a futuristic threat—it is happening today.
At the core of this challenge is defining what **wordpress security flaws exploiting ai** truly means: it means AI is systematically weaponizing the vast, ever-growing vulnerability catalog inherent in WordPress components (plugins, themes, and core). Research findings confirm that AI is enabling attackers to find and exploit WordPress weaknesses at a massive, industrialized scale, requiring next-gen security products and, often, modernized architecture (like headless or decoupled deployments) to stay ahead.

*The digital attack surface is simply too large for manual defense.* This post provides a comprehensive, solution-focused blueprint to secure your WordPress properties against this new wave of AI-powered threats in 2024. The goal isn’t just to patch, but to build layers of defense that use AI against AI.
How AI is Weaponizing WordPress Vulnerabilities
Understanding the mechanics of an AI-driven attack is the first step in constructing an effective defense. These systems automate the three phases of exploitation: reconnaissance, intrusion, and persistence.
AI-Powered Reconnaissance
Gone are the days of simple IP range scanning. Modern AI systems execute deep, targeted analysis.
- **Digital Fingerprinting at Scale:** AI systems automatically fingerprint, scan, and classify millions of WordPress sites, mapping versions, plugins, themes, and known Common Vulnerabilities and Exposures (CVEs) in hours. This massive parallel processing identifies targets based on the *exact combination* of insecure components running.
- **Zeroing in on Weakness:** AI analyzes threat intelligence data in real-time. If a new vulnerability in a popular slider plugin is published, an automated botnet can identify every site running that precise version globally within minutes, creating an instant list of high-value targets.
Enhanced Brute Force and Credential Attacks
Traditional brute-force attacks were often noisy and easily blocked by simple rate limits. AI introduces stealth and predictability.
- **Predictive Credential Stuffing:** Machine learning models optimize credential-stuffing attempts by predicting likely username/password patterns, maximizing efficiency over traditional attacks. They leverage breached data (like the recent 16 billion password leaks) to intelligently target high-value user roles.
- **Adaptive Attacks:** These systems are trained to mimic human behavior, rotate IPs effectively, and slow down attempts just enough to evade basic rate-limiting detection software. This advanced evasion technique maximizes the success rate while minimizing detection risk, distinguishing between a clumsy robot and a highly optimized script. For detailed examples of how this optimization works, see this deep dive on maximizing efficiency over traditional attacks.
The Threat of Polymorphic Malware
Perhaps the most worrying development is the use of Generative AI to create undetectable payloads.
- Generative models create code that constantly rewrites its payload (polymorphic code) using different variable names, function calls, and encodings with every injection. This means traditional signature-based scanners (which look for known malicious code patterns) are instantly rendered useless.
- *The malware becomes a shape-shifter.* An AI injection can land, execute its malicious command, and then immediately mutate its file structure, making cleanup exponentially harder.
The solution to these industrial-scale attacks is not to work harder, but to work smarter. We must embrace the automation advantage. The rest of this guide focuses on the practical steps showing **how to protect wordpress from ai hacking** by leveraging AI-powered defensive measures.
Critical Security Guide for WordPress 2024: Essential Measures
The Firewall Imperative
The first line of defense against highly optimized attacks is a powerful, AI-Enhanced Web Application Firewall (WAF). This is now a non-negotiable component of modern WordPress security, reflecting the The Firewall Imperative.
- **AI-Driven Threat Detection:** WAFs must use machine learning to detect zero-day exploits and behavior-based anomalies, rather than relying solely on known signatures. By training on massive datasets of clean and malicious traffic, AI can identify subtly dangerous requests that signature matching would miss, providing immediate protection against novel threats or slightly modified payloads.
- **Virtual Patching:** Top-tier WAFs should offer managed virtual patching. This feature shields the site against known plugin/theme vulnerabilities by intercepting and sanitizing dangerous requests *before* they reach the vulnerable component—often before the administrator even applies the official update.
- **Recommended Solutions:**
- **Cloudflare WAF:** Essential for edge protection, superior bot management, and high-capacity DDoS mitigation. Protecting traffic at the edge prevents malicious scans from ever touching your hosting environment.
- **Sucuri Website Firewall:** Known for its focus on WordPress and excellent virtual patching capabilities, along with professional malware cleanup options, critical given recent threats where hackers exploit WordPress themes to maintain persistence.
Behavioral Monitoring and Anomaly Detection
Since AI-optimized attacks mimic legitimate users, we must analyze behavior, not just code patterns.
- **Learning “Normal”:** Security scanners must continuously monitor user behavior, learning what “normal” activity looks like for your site (e.g., login times, typical geographies, administrative actions). They flag real-time deviations—a sudden change in geolocation followed by an attempt to alter critical configuration settings is immediately flagged and blocked.
- **Risk Scoring:** Modern tools must utilize AI/ML for “risk scoring” of users and requests, as highlighted by industry research on hardening WordPress security. This means every visitor interaction is assigned a risk level. A high risk score triggers immediate defense mechanisms, such as CAPTCHAs or temporary blocks, thereby protecting WordPress sites against cyberattacks using machine learning.
- **File Integrity Monitoring (FIM):** FIM is essential. It continuously detects unauthorized modifications to core WordPress files, plugin files, or the database, alerting you the instant polymorphic malware tries to establish persistence.
Hardening the Core (Operational Hygiene)
The best defenses fail if the basics are ignored. Operational hygiene remains the foundation.
- **Enforce Robust 2FA:** After massive data breaches leading to 16 billion password leaks, every administrative and editorial account *must* enforce Two-Factor Authentication (2FA). TOTP (Time-based One-Time Password) or hardware keys are preferred over SMS, which is vulnerable to SIM-swapping attacks. See more about securing accounts here.

- **Least Privilege Access:** Audit and remove all unused admin accounts immediately. Downgrade user roles to the minimum required level. If a contributor account is compromised, the impact is isolated; if an administrator account is compromised, the entire site is lost.
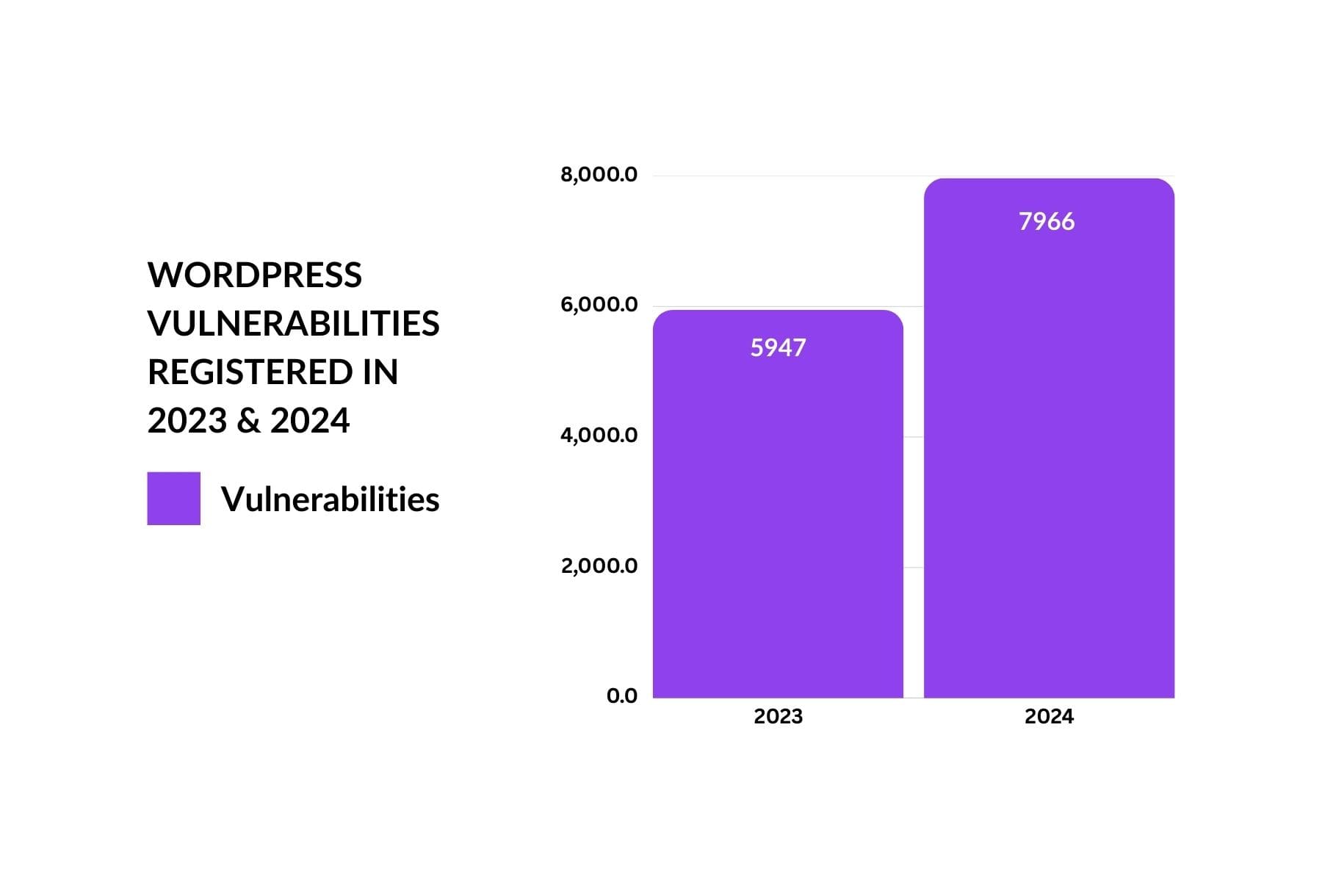
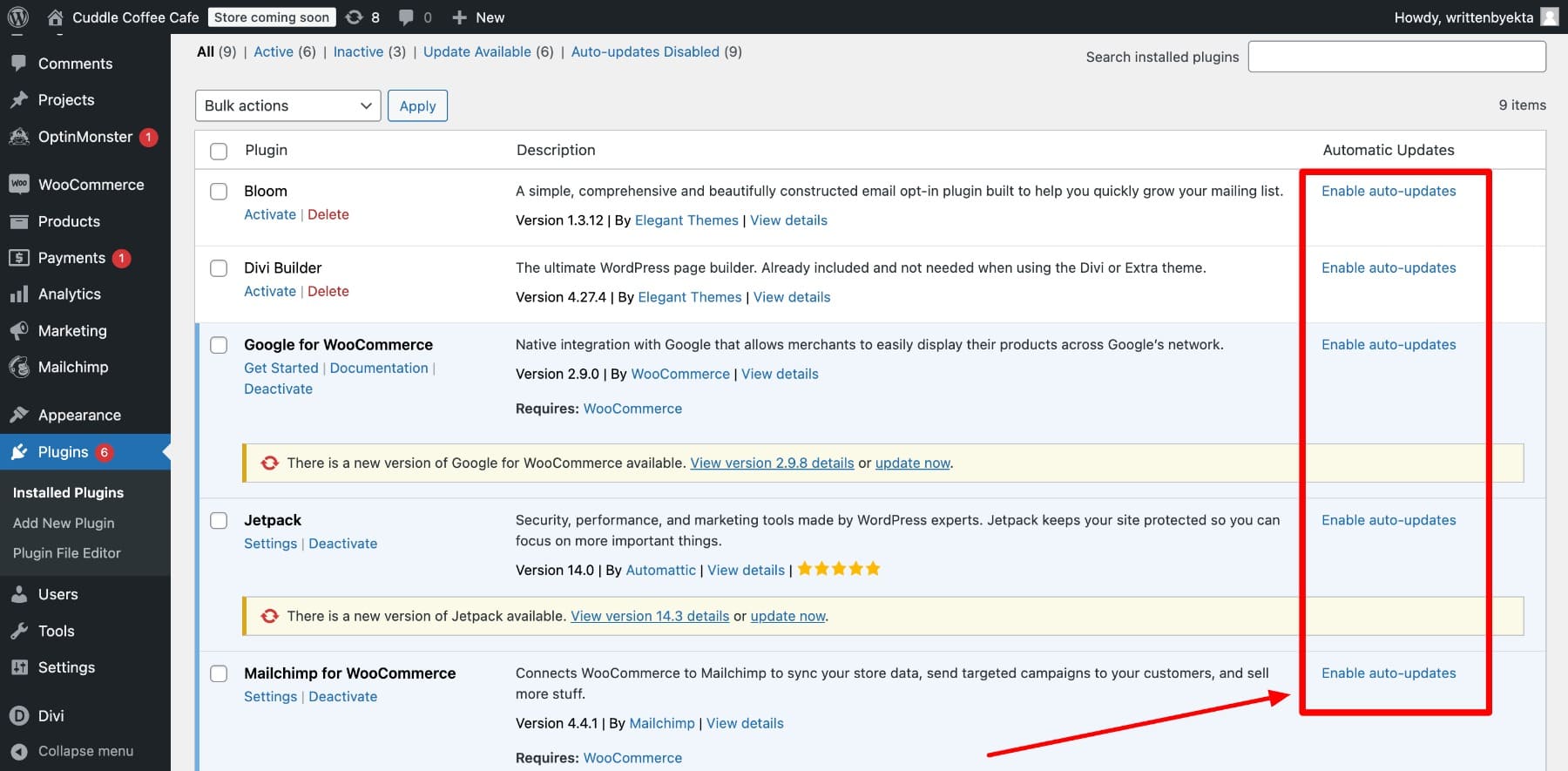
- **Aggressive, Automated Patching:** Outdated components and poor configurations are the most consistent source of breaches. Considering the 8,000 new vulnerabilities reported in 2024, manual patching is insufficient. Enable auto-updates for minor security releases and use staging environments for testing major plugin updates. For general guidelines on security and maintenance, refer to guides on Automated Patching.
Securing the Supply Chain: The Weakest Link
The vast majority of new vulnerabilities reside in third-party components, the very components that AI reconnaissance tools prioritize. Every plugin or theme installed is a dependency, adding potential complexity and risk.
The danger lies in mass exploitation: Highly publicized incidents show how hackers exploit WordPress vulnerabilities (like arbitrary installation flaws in plugins) to gain Remote Code Execution and install malicious code on thousands of sites simultaneously. Protecting against this requires rigorous control over what code runs on your server.
Strategies for Preventing Supply Chain Attacks WordPress
- **Strict Vetting Protocols:** Only use actively maintained plugins and themes sourced from the official WordPress repository or highly reputable, audited commercial developers. *Never* use “nulled” or pirated versions, which are often pre-packed with backdoors.
- **Dependency Tracking (SCA):** Use automated tools or services to map every installed component against public CVE databases to highlight risk levels in real-time. Managed security services are excellent for providing this continuous vulnerability reporting per plugin, helping you proactively quarantine or replace risky components.
- **Code Integrity Monitoring:** Deploy dedicated FIM to detect two key attack vectors: when malicious code is injected into third-party files, or when critical theme files like `functions.php` are altered—a common method for creating persistent, signature-evading backdoors.
- **Minimize Installation Count:** If you don’t use a plugin, uninstall it. Fewer dependencies mean a smaller attack surface for AI reconnaissance tools to leverage.

Architectural Defense: Adopting Headless WordPress
While optimizing traditional WordPress security is essential, the ultimate defense against high-speed, automated threats is architectural isolation. Decoupling the presentation layer from the data layer is a core component of staying ahead in 2024 and reflects broader architectural defense trends.
**What is Headless WordPress?**
In a headless setup, WordPress runs in a secured backend (the CMS), handling content creation and management. A separate, modern frontend (often built with frameworks like Next.js, Gatsby, or Vue.js) then serves the content to the public via highly controlled APIs (REST or GraphQL).
**Security Benefits:**
- **Reduced Attack Surface:** The vast majority of the attack surface—the dynamic PHP environment, the entire `/wp-admin` dashboard, and critical plugin endpoints—is no longer publicly exposed to anonymous web traffic. Attackers cannot easily scan for version numbers or execute PHP exploits.
- **Isolation and Containment:** If the frontend is compromised (e.g., via a sophisticated XSS attack), the breach is isolated to the presentation layer. The core CMS, database, and administration panel remain protected, making it significantly harder for attackers to gain Remote Code Execution or steal sensitive data.
- **Static Immunity:** By compiling the frontend into static files served by a CDN, you eliminate server-side vulnerabilities for public viewing, achieving near-perfect immunity against many common WordPress attack types.
Criteria for Selecting the Best Headless CMS for WordPress Security
When choosing the **best headless cms for wordpress security**, focus on these attributes:

- **Focus on API Security:** The security burden shifts to the API connecting the CMS and the frontend. Look for systems that support fine-grained API permissions, strong token-based authentication (JWT, OAuth2), and native rate-limiting/protection against GraphQL/REST abuse.
- **Operational Security:** Ensure the solution integrates easily with Identity Providers (SSO) for centralized user management and maintains comprehensive security audit logs to track internal changes and API interactions.
- **Performance and Edge Integration:** The setup should allow for serving static/compiled files via a global Content Delivery Network (CDN) to leverage their superior DDoS protection and edge security rulesets (e.g., Cloudflare, Akamai). This offloads risk from your origin server entirely.
Recommended Security Toolkit: Products and Services
Defending against AI requires deploying specialized tools optimized for speed and behavioral analysis.
Top-Tier WAFs and Edge Security
- **Cloudflare:** Essential for global protection. Their managed WAF rulesets, advanced bot management, and DDoS protection operate before traffic reaches your host, mitigating the bulk of automated attacks.
- **Sucuri:** Highly recommended for its focus on WordPress/CMS protection, industry-leading virtual patching capabilities, and professional malware remediation services—critical if an AI-optimized attack does breach your defenses.
AI-Powered Plugin Suites
- **Wordfence/Patchstack:** These are essential tools for application-level WAF, real-time threat intelligence feeds, and advanced malware scanning/file integrity checks. Patchstack, in particular, focuses heavily on providing real-time vulnerability intelligence for the entire plugin ecosystem.
- **Behavioral Focus:** When evaluating security plugins, prioritize solutions advertising Behavioral Analysis. These features are critical for defending against AI-optimized attacks that mimic human patterns and use polymorphic code.
Security-Focused Managed Hosting
For organizations that cannot staff dedicated security teams, migrating to managed hosts (Kinsta, WP Engine, Pagely) is a vital defense strategy. They provide:

- Built-in server-level WAFs optimized for WordPress.
- Automatic, aggressive patching of the core CMS and server OS.
- Container isolation (ensuring one compromised site doesn’t affect others).
- Professional security response as part of the service level agreement.
Summary and Final Checklist
The transformation in the threat landscape is complete. AI allows attackers to iterate and weaponize flaws at speed, eroding the value of outdated, purely signature-based defenses. Security is no longer a static configuration; it is a continuous, automated, and AI-enabled process.
Your immediate action plan should include:
- Deploying a modern, behavioral WAF (Cloudflare or Sucuri).
- Enforcing 2FA and least privilege across *all* accounts.
- Securing the supply chain via strict vetting and continuous integrity checks.
- Evaluating decoupling (Headless WordPress) for maximum architectural defense.
The goal is simple: turn the automation attackers rely on into your strongest line of defense. Constant vigilance and updated tools are the price of security in the age of AI.
Frequently Asked Questions
Q: What is the single biggest security risk WordPress faces from AI?
The single biggest risk is the *speed* and *scale* of exploitation. AI systems rapidly scan millions of sites to match newly published CVEs (vulnerabilities) to the exact combination of outdated themes and plugins running on a server. This dramatically reduces the window of time site owners have to patch—often from weeks to mere hours.
Q: How do I know if a security plugin uses AI?
Look for features that go beyond simple signature matching. Key indicators of AI/ML integration include “Behavioral Analysis,” “Anomaly Detection,” “Bot Management,” “Risk Scoring,” and “Zero-Day Exploit Protection.” These systems learn what is normal for your site and flag deviations, rather than just blocking known bad inputs.
Q: Is going headless really necessary for all WordPress sites?
No, it’s not necessary for all sites, but it is highly recommended for high-traffic, mission-critical, or high-value enterprise properties that are frequent targets. For a small blog, traditional hardening (WAF, 2FA, rigorous patching) is usually sufficient. Headless is an advanced architectural defense that minimizes risk at the expense of setup complexity.
Q: Can AI write malware that current scanners can’t detect?
Yes. AI’s ability to generate polymorphic code means it can constantly change the structure and encoding of the payload. Since most basic scanners rely on looking for known malicious code signatures, these AI-generated, ever-changing payloads often bypass them initially. This is why defensive AI (behavioral monitoring) and File Integrity Monitoring (FIM) are now crucial—they detect the *effect* of the malware (unauthorized changes), not just the signature of the code itself.