Navigating the Evolving Digital Threat Landscape: Insights from Cloudflare Cyber Threat Statistics Q2 2025 and Beyond
Estimated reading time: 12 minutes
Key Takeaways
- Cyber threats are escalating in complexity and scale, driven by multi-vector campaigns, AI, and a digital-first economy.
- Cloudflare’s Q2 2025 insights are critical, highlighting persistent threats like **DDoS attacks**, **bot traffic**, and **application vulnerabilities**.
- Global trends reveal AI-powered malware, sophisticated multi-vector attacks, and increased geopolitical influence in cyber warfare.
- **Ransomware** remains a dominant threat, evolving with double/triple extortion and AI-augmented variants.
- **Mobile devices** are growing targets, demanding robust security measures like MDM and MFA.
- AI plays a dual role, empowering both attackers and defenders, leading to an accelerating “AI arms race”.
- Proactive defense, continuous vigilance, and adaptive strategies are paramount for navigating the 2025 threat landscape.
Table of contents
- Navigating the Evolving Digital Threat Landscape: Insights from Cloudflare Cyber Threat Statistics Q2 2025 and Beyond
- Key Takeaways
- Introduction: Navigating the Evolving Digital Threat Landscape
- I. Unpacking Cloudflare Cyber Threat Statistics Q2 2025: Key Trends and Attack Vectors
- Detailed analysis of key data points and trends revealed by Cloudflare cyber threat statistics Q2 2025
- Insights into Targeted Industries and Geographic Hotbeds
- Comparison of Q2 2025 Data with Previous Quarters to Highlight Shifts or Accelerations in Threat Patterns
- II. Global Cyber Attack Trends 2025: A Worldwide Perspective on Escalating Threats
- Discussion on the overall increase in attack sophistication and multi-vector campaigns
- Emerging Geopolitical Influences on Cyber Warfare and State-Sponsored Attacks
- Analysis of Supply Chain Attacks and Their Growing Impact Across Various Sectors
- III. The Persistent Surge: Why Ransomware Attacks Increase in 2025
- Dedicated section exploring the reasons behind the continued and amplified ransomware attacks increase 2025
- Industries Most Targeted
- Economic and Operational Impact of Ransomware
- IV. Safeguarding Your Handheld: Mobile Device Security Threats 2025
- Examination of the unique and evolving landscape of mobile device security threats 2025
- Why Mobile Devices are Increasingly Lucrative Targets for Cybercriminals
- Best Practices and Mitigation Strategies for Individuals and Organizations
- V. The Future of Conflict: AI Cyber Warfare Predictions 2025
- Probing the anticipated role of Artificial Intelligence in the future of cybersecurity and AI cyber warfare predictions 2025
- Ethical Considerations and the Ongoing “AI Arms Race”
- Quantum Computing Threats (Though Nascent)
- Conclusion: Fortifying Defenses in a Volatile Digital Era
- Frequently Asked Questions
Introduction: Navigating the Evolving Digital Threat Landscape
In an increasingly interconnected world, the digital realm has become a fertile ground for both innovation and exploitation. Cyber threats are not merely increasing in frequency; they are rapidly increasing in both complexity and scale, with attackers employing sophisticated multi-vector campaigns, leveraging AI, and targeting a global, digital-first economy. This rise in sophistication and volume requires organizations to remain vigilant and informed (Source: https://www.splashtop.com/blog/cybersecurity-trends-2025; https://cloud.google.com/security/resources/cybersecurity-forecast; https://www.sentinelone.com/cybersecurity-101/cybersecurity/cyber-security-trends/). For a deeper dive into these broad trends, consider the insights from Explosive Cybersecurity Threats: Key Trends, Predictions, and Defense Strategies for 2025. The landscape is dynamic, and failing to adapt is no longer an option.

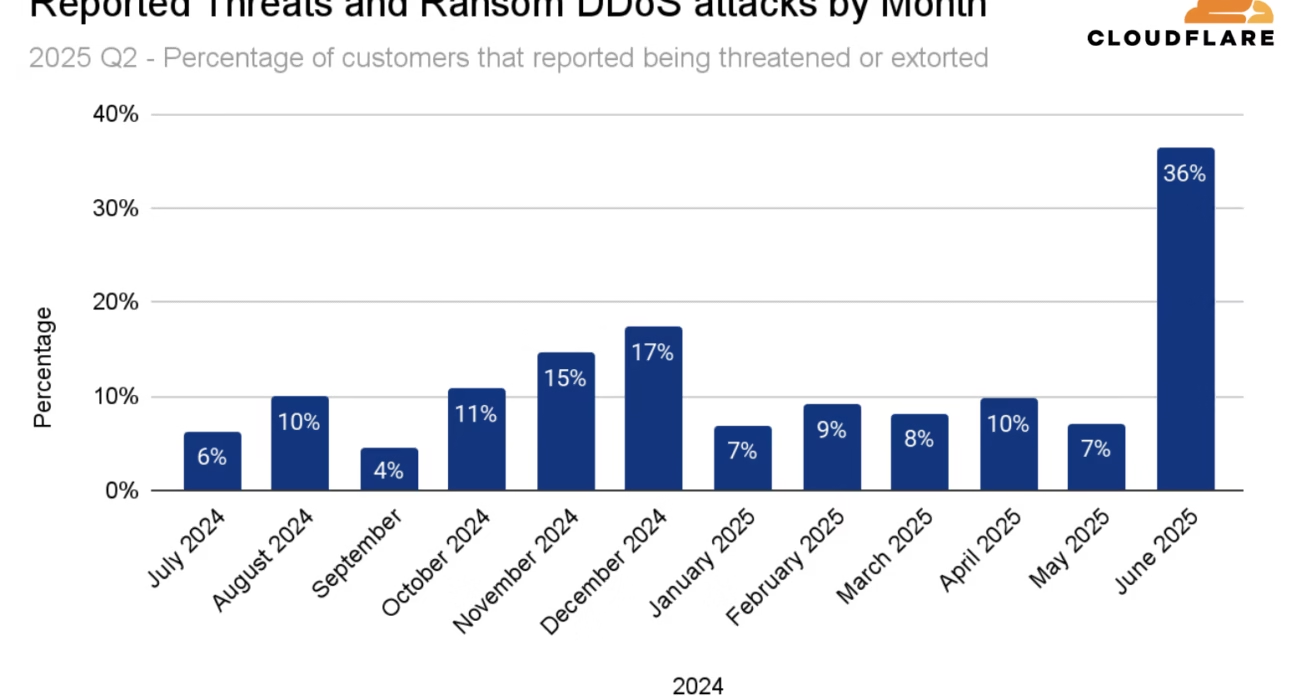
This post introduces the core focus: a deep dive into Cloudflare cyber threat statistics Q2 2025. Due to their expansive global network, Cloudflare plays a pivotal role in observing, mitigating, and reporting on real-time cyber security challenges. Their data provides critical, real-time insights that are invaluable for understanding the current threat environment.
Beyond specific Cloudflare statistics, this comprehensive post will broaden its scope to cover overarching global cyber attack trends 2025, the alarming rise of ransomware attacks increase 2025, the growing concern of mobile device security threats 2025, and the transformative, dual-edged impact of AI cyber warfare predictions 2025. Our aim is to provide technical context, actionable insights, and practical takeaways that organizations can apply to fortify their defenses in 2025 and well into the future.
I. Unpacking Cloudflare Cyber Threat Statistics Q2 2025: Key Trends and Attack Vectors
Detailed analysis of key data points and trends revealed by Cloudflare cyber threat statistics Q2 2025
While specific Q2 2025 Cloudflare data is not yet publicly available, we can synthesize common and anticipated trends reported by leading cybersecurity authorities to infer what Cloudflare’s report would likely highlight. The consistent escalation in cyberattacks indicates a future where traditional defenses are increasingly challenged.

**Most Prevalent Attack Vectors Identified:**
- DDoS Attacks: Distributed Denial of Service (DDoS) attacks remain among the most prevalent threats. Attackers are increasingly using powerful botnets and leveraging cloud infrastructure’s scale for amplification, making these attacks larger, more sustained, and more complex to mitigate. They aim to overwhelm systems, causing service outages and significant financial losses.
- Bot Traffic and API Abuses: Malicious bot traffic constitutes a significant portion of internet activity. Attackers automate attacks on login endpoints, execute credential stuffing (attempting to log in with stolen username/password pairs), exploit poorly secured APIs, and target business logic vulnerabilities. This often results in data leaks, account takeovers, and service interruptions (Source: https://cloud.google.com/security/resources/cybersecurity-forecast). The sheer volume of compromised credentials can be staggering; for guidance on managing such breaches, refer to What to Do After the 16 Billion Password Leak: A Critical Security Guide.
- Application Vulnerabilities: The exploitation of zero-day attacks (previously unknown vulnerabilities) and misconfigurations in web applications and cloud-native applications continues to be a significant entry point for adversaries (Source: https://www.sentinelone.com/cybersecurity-101/cybersecurity/cyber-security-trends/). As software development cycles accelerate, the window for identifying and patching these flaws shrinks, making them prime targets.
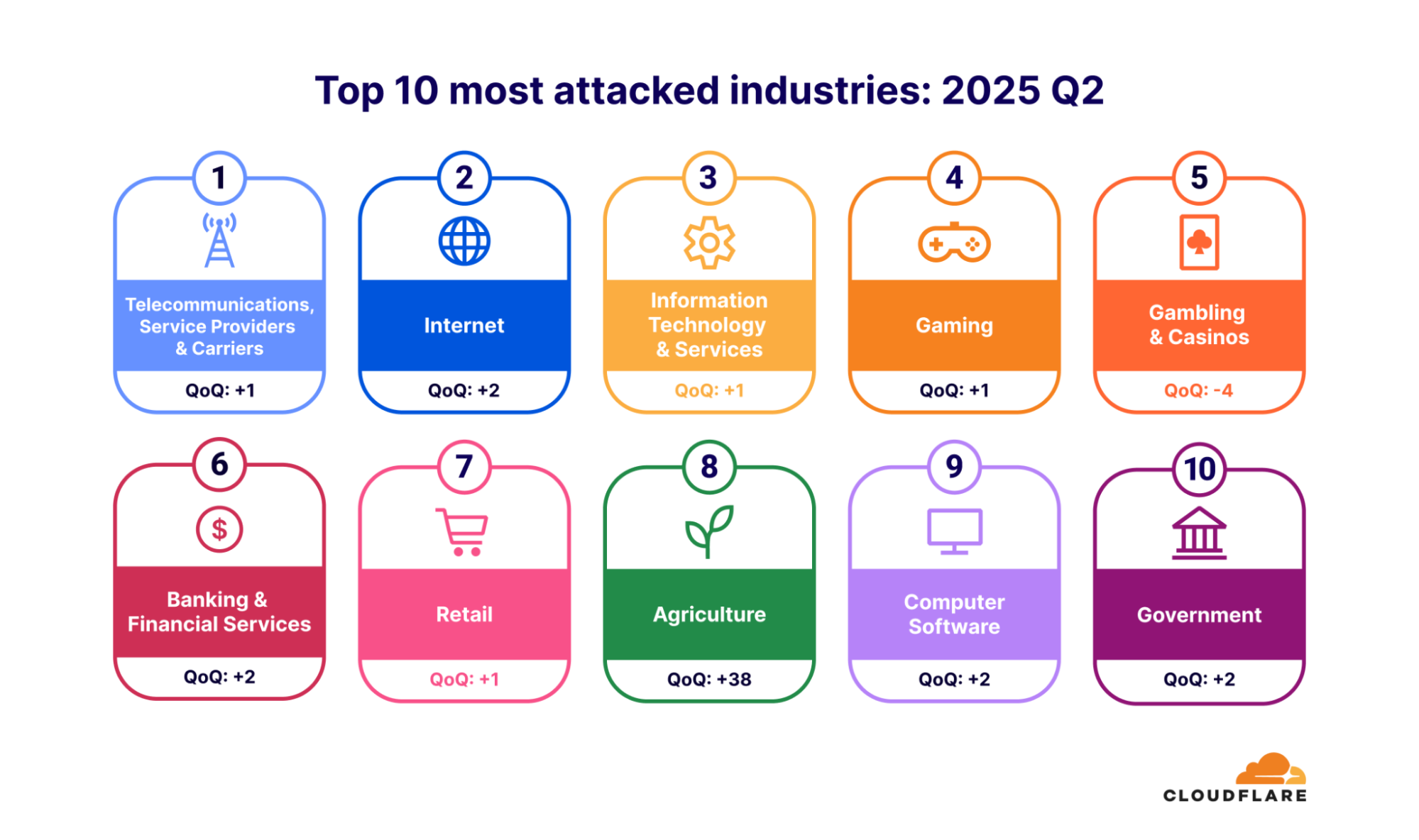
Insights into Targeted Industries and Geographic Hotbeds
Multiple industry reports confirm that critical infrastructure and operational technology (OT) sectors—such as energy, healthcare, manufacturing, and finance—have become prime targets for cyber-attacks (Source: https://www.honeywell.com/us/en/news/featured-stories/2025/01/cybersecurity-trends-blog). The disruption potential in these sectors is immense, leading to significant national security and economic stability concerns. These attacks are not just about data theft but about causing systemic breakdown.
Geographically, hotspots for cyber activity often include North America, EMEA (Europe, Middle East, and Africa), and APAC (Asia-Pacific). This is driven by a confluence of factors including economic importance, technological advancement, and geopolitical tensions, which incite both sophisticated criminal enterprises and state-linked groups to operate actively within these regions.
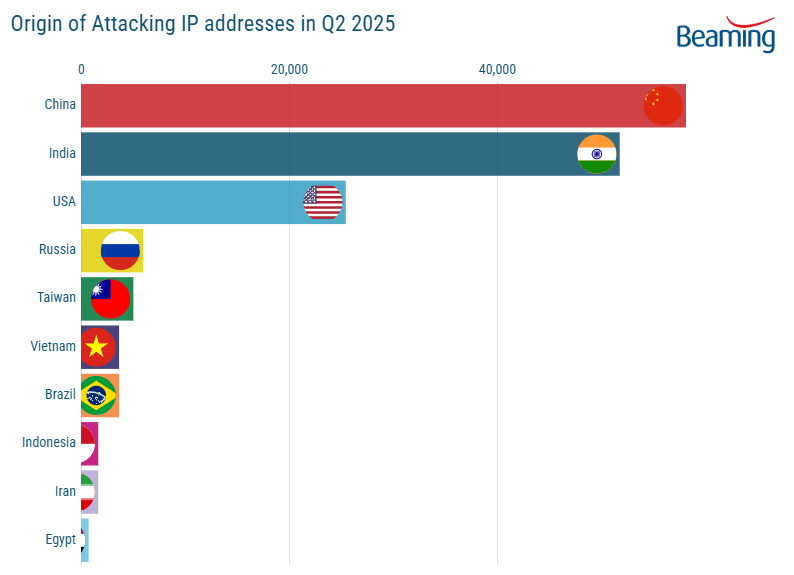
Comparison of Q2 2025 Data with Previous Quarters to Highlight Shifts or Accelerations in Threat Patterns
The data suggests a consistent trend: cyberattacks are not just increasing in volume but also in their strategic depth. We are seeing a growing percentage of multi-stage and AI-augmented attacks, indicating a fundamental shift towards more complex, blended threat campaigns that are harder to detect and defend against. This means attackers are no longer relying on single exploits but orchestrating intricate sequences of attacks.

Furthermore, DDoS attack sizes and durations are consistently trending upwards, with attackers combining application-layer and volumetric methods for greater impact. This synergistic approach maximizes disruption and makes mitigation far more challenging for targeted organizations. A particularly concerning trend echoed by several 2025 forecasts is a significant increase in attacks exploiting supply chain vulnerabilities (Source: https://www.splashtop.com/blog/cybersecurity-trends-2025; https://cloud.google.com/security/resources/cybersecurity-forecast). This signifies a move towards targeting weak links in broader ecosystems rather than direct assaults on primary targets, leading to a ripple effect of compromise.
II. Global Cyber Attack Trends 2025: A Worldwide Perspective on Escalating Threats
Broadening our scope from Cloudflare’s specific data, it’s evident that **global cyber attack trends 2025** paint a picture of accelerating threats and a worldwide surge in malicious cyber activity. The interconnectedness of global economies means that a breach anywhere can quickly reverberate everywhere.
Discussion on the overall increase in attack sophistication and multi-vector campaigns
**AI-Powered Malware and Social Engineering Tools:** Artificial Intelligence (AI) is undoubtedly propelling the volume and sophistication of cyberattacks at an unprecedented rate. AI enables the creation of polymorphic malware (malware that changes its code to avoid detection), deepfake phishing (using AI to create realistic fake voices or videos for highly convincing social engineering), and rapid vulnerability exploitation (Source: https://www.splashtop.com/blog/cybersecurity-trends-2025; https://cloud.google.com/security/resources/cybersecurity-forecast; https://www.sentinelone.com/cybersecurity-101/cybersecurity/cyber-security-trends/). This significantly lowers the barrier for entry for less skilled attackers while amplifying the capabilities of advanced persistent threats (APTs).
**Rise in Multi-Vector Attacks:** Modern campaigns rarely rely on a single attack method. Instead, they often combine multiple attack types, such as ransomware, data exfiltration, DDoS attacks, and lateral movement within compromised networks, all designed to maximize disruption and impact. This coordinated approach makes incident response far more complex and costly.
Emerging Geopolitical Influences on Cyber Warfare and State-Sponsored Attacks
Geopolitical tensions are increasingly fueling state-sponsored cyber operations. Major actors like Russia, China, Iran, and North Korea are actively targeting strategic sectors and critical national infrastructure globally (Source: https://cloud.google.com/security/resources/cybersecurity-forecast). These operations are not always for financial gain; they often aim for espionage, intellectual property theft, or even the disruption of national services to achieve political objectives, blurring the lines between traditional warfare and cyber conflict.
Analysis of Supply Chain Attacks and Their Growing Impact Across Various Sectors
Supply chain attacks have become alarmingly common, posing widespread risks across entire value chains. These attacks exploit trust relationships between an organization and its vendors, partners, or software suppliers. They are particularly prevalent in sectors like software development, critical manufacturing, and cloud services, where a single breach can compromise numerous downstream entities (Source: https://cloud.google.com/security/resources/cybersecurity-forecast). The SolarWinds incident serves as a stark reminder of the devastating potential of such attacks, making robust vendor risk management an absolute necessity for 2025 and beyond.
III. The Persistent Surge: Why Ransomware Attacks Increase in 2025
Dedicated section exploring the reasons behind the continued and amplified ransomware attacks increase 2025
The trend of ransomware attacks increase 2025 is arguably the most concerning aspect of the current threat landscape. Ransomware continues to be the single most disruptive cybercrime threat, constantly evolving in its tactics and scale (Source: https://cloud.google.com/security/resources/cybersecurity-forecast; https://www.splashtop.com/blog/cybersecurity-trends-2025). What was once a simple data encryption attack has morphed into a complex extortion ecosystem.

**Proliferation of Double and Triple Extortion Models:** Attackers are no longer just encrypting data and demanding payment for decryption keys. They are increasingly employing “double extortion,” where they first steal sensitive files and then encrypt the data, threatening public leaks if the ransom is not paid. Even more aggressive is “triple extortion,” which adds a DDoS attack against the victim’s public-facing assets or informs clients/partners of the breach to apply immense pressure for payment (Source: https://www.splashtop.com/blog/cybersecurity-trends-2025). This multi-pronged approach significantly increases the stakes for victims.
**Role of Ransomware-as-a-Service (RaaS):** Ransomware-as-a-Service (RaaS) operations have dramatically lowered the barrier for entry into cybercrime. By renting pre-built ransomware tools, infrastructure, and even support services, less skilled criminals can launch sophisticated and widespread attacks (Source: https://www.splashtop.com/blog/cybersecurity-trends-2025). This democratization of cyber weaponry has led to an explosion in ransomware incidents globally.
**New Variants Leveraging AI:** A truly concerning development is the emergence of new ransomware variants that use AI to evade detection by traditional security software, intelligently target backup systems for maximum impact, and automate lateral movement within compromised networks (Source: https://www.sentinelone.com/cybersecurity-101/cybersecurity/cyber-security-trends/). This AI-driven sophistication makes these attacks far more stealthy and destructive.
Industries Most Targeted
Sectors such as healthcare, manufacturing, critical infrastructure, and education are particularly vulnerable to ransomware. Their critical nature often means they cannot afford significant downtime, making them more likely to pay ransoms. Furthermore, these sectors frequently operate with legacy systems, complex IT environments, and often insufficient cybersecurity budgets, making them softer targets.
Economic and Operational Impact of Ransomware
The impact of ransomware extends far beyond the immediate ransom payment. Organizations incur significant financial losses from:
- Recovery costs, which can far exceed the ransom demand.
- Prolonged operational downtime, leading to lost revenue and productivity.
- Potential regulatory penalties due to data breaches (e.g., GDPR, HIPAA fines).
- Severe reputational damage, eroding customer and stakeholder trust.
These consequences affect businesses and critical infrastructure globally, underscoring the urgency of robust anti-ransomware strategies.
IV. Safeguarding Your Handheld: Mobile Device Security Threats 2025
Examination of the unique and evolving landscape of mobile device security threats 2025
The landscape of mobile device security threats 2025 is intensifying dramatically. As smartphones become ubiquitous and IoT (Internet of Things) connected devices proliferate (e.g., The Rise of Unstoppable AI-Powered Smart Homes: Revolutionary Trends Shaping the Future), attackers are increasingly exploiting their vulnerabilities. This is particularly true for advanced mobile devices, as explored in Unstoppable AI-Powered Smartphones: The Revolutionary Future of Mobile Technology Unveiled. Our handheld companions are becoming primary targets.
**Sophisticated Mobile Malware:** Mobile malware is becoming increasingly sophisticated, utilizing advanced obfuscation techniques (to hide its malicious code) and privilege escalation methods (to gain higher access permissions on devices). This allows malware to operate stealthily, often undetected by basic antivirus solutions, leading to data theft or device control.
**Phishing and Smishing Campaigns:** Phishing (via email) and smishing (via SMS/text messages) campaigns specifically target mobile users through SMS, popular messaging apps, and malicious QR codes. These campaigns are highly effective, often leading to credential theft, malware installation, or deceptive financial transactions (Source: https://www.splashtop.com/blog/cybersecurity-trends-2025; https://www.sentinelone.com/cybersecurity-101/cybersecurity/cyber-security-trends/). The casual nature of mobile communication makes users more susceptible.

**Insecure Mobile Applications and Poor Endpoint Hygiene:** Poorly secured mobile applications and inadequate mobile device hygiene (e.g., outdated operating systems, lack of security software, side-loading apps) can expose enterprise networks to significant breaches (Source: https://www.splashtop.com/blog/cybersecurity-trends-2025). Each mobile device connected to a corporate network represents a potential entry point for attackers.
Why Mobile Devices are Increasingly Lucrative Targets for Cybercriminals
Mobile devices are constant companions, often poorly secured by users, hold a wealth of sensitive work and personal data, and serve as direct bridges into corporate resources and networks. Their always-on, always-connected nature, combined with user habits that prioritize convenience over security, make them incredibly attractive targets for cybercriminals seeking data, access, or financial gain.
Best Practices and Mitigation Strategies for Individuals and Organizations
To combat these threats, comprehensive strategies are required:
- Advise on enforcing Mobile Device Management (MDM) solutions for organizations, which allow centralized policy enforcement, app distribution, and remote wiping.
- Ensuring regular patching and updates of operating systems and applications is critical, as these often contain security fixes.
- Rigorous app vetting processes, especially for enterprise app stores, to prevent malicious applications from gaining a foothold.
- Comprehensive user training on mobile security awareness is paramount, teaching users to recognize phishing attempts and practice safe browsing.
- Mandatory multi-factor authentication (MFA) for all accounts, especially those accessing corporate resources, adds a crucial layer of security (Source: https://www.splashtop.com/blog/cybersecurity-trends-2025; https://www.sentinelone.com/cybersecurity-101/cybersecurity/cyber-security-trends/).
V. The Future of Conflict: AI Cyber Warfare Predictions 2025
Probing the anticipated role of Artificial Intelligence in the future of cybersecurity and AI cyber warfare predictions 2025
Artificial Intelligence (AI) is not just a tool; it’s a transformative force reshaping the entire cybersecurity landscape. The AI cyber warfare predictions 2025 indicate a future where AI’s role in both offensive and defensive operations becomes increasingly central and sophisticated.

**AI Transforming Offensive Operations:** Attackers are leveraging AI for automated reconnaissance (gathering vast amounts of information about targets rapidly), accelerated vulnerability discovery (identifying flaws in software with unprecedented speed), and crafting highly convincing social engineering lures (e.g., AI-generated phishing emails or voice calls that are almost indistinguishable from legitimate communications) (Source: https://www.splashtop.com/blog/cybersecurity-trends-2025; https://cloud.google.com/security/resources/cybersecurity-forecast; https://www.sentinelone.com/cybersecurity-101/cybersecurity/cyber-security-trends/). This significantly enhances the scale, speed, and stealth of attacks, making them far more effective.
**Adaptive and Evasive Malware:** Malware itself is becoming more adaptive and evasive, with AI-based payloads that can learn from their environment and change their behavior in real-time to bypass traditional, signature-based defenses. These intelligent threats pose a grave challenge to legacy security systems.
**The Dual Role of AI in Defense:** Fortunately, defenders are also deploying AI to counter these threats. AI is crucial for enhanced threat detection, automated incident response (e.g., automatically isolating compromised systems or blocking malicious traffic), and predictive analytics (anticipating future attacks based on observed patterns). This enables faster and more accurate incident triage and containment, reducing reaction times from hours to minutes, or even seconds (Source: https://www.splashtop.com/blog/cybersecurity-trends-2025; https://cloud.google.com/security/resources/cybersecurity-forecast). For more on this, see Breakthrough AI Cyber Defense: Revolutionizing Modern Cybersecurity.

Ethical Considerations and the Ongoing “AI Arms Race”
The escalating “AI arms race” between offensive and defensive capabilities raises critical ethical concerns. Issues around attack attribution (determining who launched an AI-driven attack), cyber stability (the risk of unintended escalation), and the increasing speed and scale of digital conflict are paramount. Regulatory bodies are beginning to grapple with these complexities, as highlighted in guides like Understanding New AI Regulations: A Crucial Guide for Businesses Navigating Global Rules and the Impact of the EU AI Act and analyses on Critical AI Challenges Tech Industry 2025: Future Trends and Upcoming Regulations. Ensuring responsible AI development and deployment is crucial for global cyber peace.
Quantum Computing Threats (Though Nascent)
Though still nascent, breakthroughs in quantum computing are a growing concern. Experts anticipate that sufficiently powerful quantum computers could potentially undermine current cryptographic protections, including those securing internet communications and data storage (Source: https://www.sentinelone.com/cybersecurity-101/cybersecurity/cyber-security-trends/). This motivates early adoption of post-quantum algorithms to secure data for the future, a proactive measure against a threat that, while not imminent, requires long-term strategic planning.
Conclusion: Fortifying Defenses in a Volatile Digital Era
The insights gleaned from hypothetical Cloudflare cyber threat statistics Q2 2025 and the broader global cyber attack trends 2025 undeniably confirm that we have entered a new era of sophisticated, fast-evolving cyber risk. The persistent and amplified challenges posed by the ransomware attacks increase 2025 underscore the financial and operational devastation these threats can wreak. Concurrently, the specific vulnerabilities presented by mobile device security threats 2025 highlight the expanding attack surface due to our reliance on handheld technology.
Perhaps most significantly, the transformative impact of AI cyber warfare predictions 2025 on both offensive and defensive strategies makes continuous vigilance and adaptability not just beneficial, but absolutely paramount. AI is not just changing how businesses operate, as explored in How AI is Transforming Businesses: A Comprehensive Guide for 2025, but also how they must protect themselves. Understanding these detailed trends is crucial for all organizations committed to building resilient digital defenses in 2025 and beyond. It highlights that continuous vigilance, investment in adaptive security strategies, and leveraging AI for both offense and defense are now table stakes (Source: https://www.splashtop.com/blog/cybersecurity-trends-2025; https://www.honeywell.com/us/en/news/featured-stories/2025/01/cybersecurity-trends-blog; https://cloud.google.com/security/resources/cybersecurity-forecast; https://www.sentinelone.com/cybersecurity-101/cybersecurity/cyber-security-trends/). For everyday users looking to improve their own digital safety, fundamental Cybersecurity Tips for Everyday Users: How to Stay Safe Online remain essential in this increasingly hazardous digital world.
Frequently Asked Questions
Q1: What are the primary attack vectors Cloudflare’s Q2 2025 report would likely highlight?
A1: Based on current and anticipated trends, Cloudflare’s Q2 2025 report would likely emphasize the continued prevalence of DDoS attacks, sophisticated bot traffic and API abuses (including credential stuffing), and the exploitation of various application vulnerabilities, especially zero-days and misconfigurations in web and cloud-native applications. These vectors consistently represent major threats to online services.
Q2: Why is ransomware considered the most disruptive cybercrime threat in 2025?
A2: Ransomware continues its reign due to its evolving tactics, particularly the widespread adoption of “double” and “triple extortion” models that involve data theft, encryption, and additional pressure tactics like DDoS attacks. The proliferation of Ransomware-as-a-Service (RaaS) has also significantly lowered the barrier to entry for criminals, while new AI-augmented variants make attacks harder to detect and recover from, causing immense financial and operational damage to victims.
Q3: How is AI impacting both cyberattacks and cybersecurity defenses in 2025?
A3: AI is a double-edged sword in cybersecurity. For attackers, AI enables automated reconnaissance, faster vulnerability discovery, and the creation of highly convincing deepfake phishing and social engineering campaigns. On the defensive side, AI is crucial for enhanced threat detection, automated incident response, and predictive analytics, allowing defenders to identify and mitigate threats with greater speed and accuracy. This creates an ongoing “AI arms race” between malicious actors and security professionals.
Q4: What makes mobile devices increasingly lucrative targets for cybercriminals?
A4: Mobile devices are attractive targets because they are constant companions, often contain vast amounts of sensitive personal and corporate data, and serve as direct bridges into enterprise networks. Many users also tend to apply fewer security measures on their mobile devices compared to traditional computers, making them easier entry points for sophisticated mobile malware, phishing/smishing campaigns, and attacks exploiting insecure mobile applications.
Q5: What are the key strategies organizations should adopt to fortify their defenses in 2025?
A5: Organizations must adopt a multi-layered and adaptive security strategy. Key elements include investing in advanced threat intelligence, implementing robust Mobile Device Management (MDM) and Multi-Factor Authentication (MFA), regularly patching and updating all systems, enhancing employee security awareness training, and leveraging AI-driven security solutions for faster detection and response. Proactive defense, continuous vigilance, and a commitment to adapting to evolving threats are absolutely critical.