Blockchain Identity Verification Tools: The Future of Secure Digital Identity
Estimated reading time: 15 minutes
Key Takeaways
- Blockchain identity verification tools offer enhanced security through decentralization and immutability, eliminating single points of failure.
- Users gain privacy and control over their identity data with features like selective disclosure and self-sovereign identity.
- Advanced privacy tech such as zero-knowledge proofs enables proving claims without revealing sensitive information.
- Authenticity AI blockchain integrations enhance verification with biometric analysis and real-time fraud detection.
- Real-world applications span financial services, healthcare, travel, voting, and education, solving actual identity challenges.
Table of contents
- Opening & Problem Statement
- What Are Blockchain Identity Verification Tools?
- How Blockchain Technology Secures Digital Identity
- The Verification Process: How It Works in Practice
- Core Benefits: Why Blockchain Identity Verification Tools Matter
- Advanced Privacy Technologies Powering Blockchain Identity Systems
- The Role of AI in Enhancing Authenticity & Verification
- Real-World Applications: Where Blockchain Identity Verification Tools Solve Actual Problems
- Current Tools & Technologies: Notable Platforms & Standards
- Overcoming Challenges: Adoption, Standards & the Road Ahead
- Frequently Asked Questions
Opening & Problem Statement
In today’s digital world, proving who you are online is fraught with risks. Blockchain identity verification tools emerge as a revolutionary solution to the persistent challenges of centralized identity systems. Users face critical problems:
- Fraud and identity theft in digital transactions, leading to financial loss and privacy invasion.
- Data breaches exposing centralized databases, as seen in numerous high-profile incidents.
- Lack of user control over personal identity information, with intermediaries holding all the power.
- Vulnerable intermediaries managing sensitive data, creating single points of failure.
These issues matter because they erode trust, cause financial harm, and compromise privacy. Traditional systems rely on centralized authorities, but as research shows, this model is inherently vulnerable. Blockchain offers a paradigm shift, moving towards secure digital ID systems where users are in control.

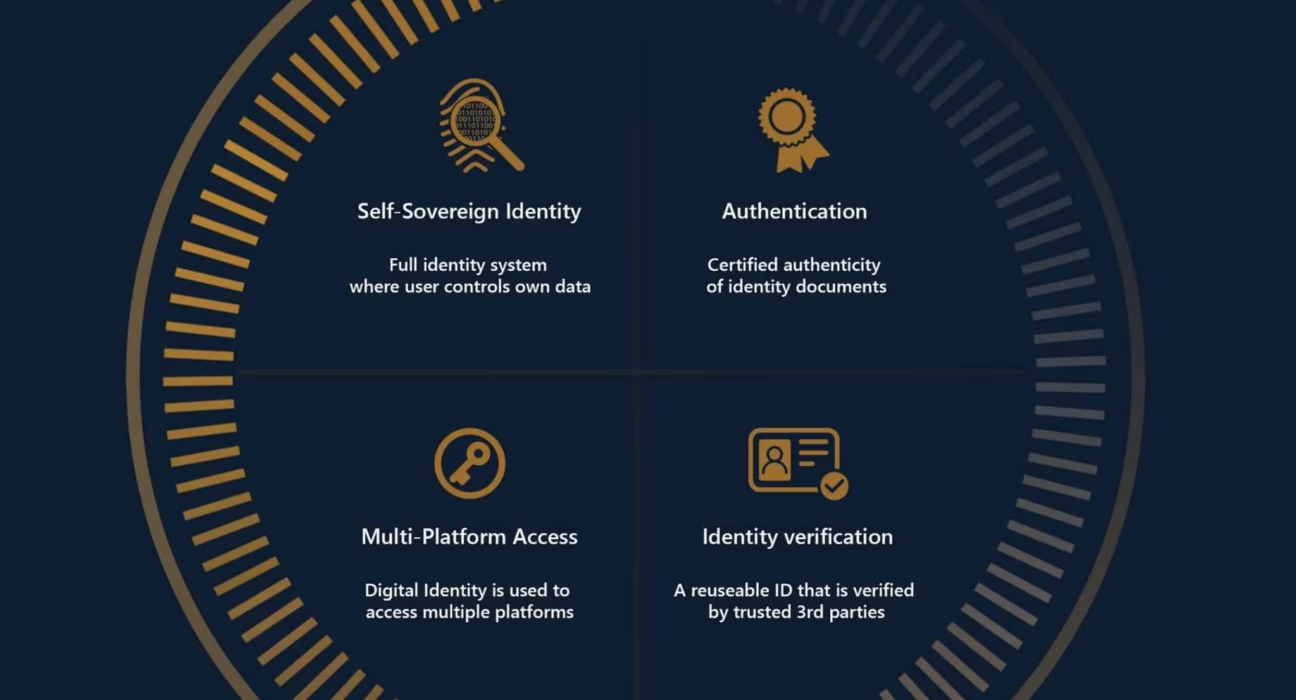
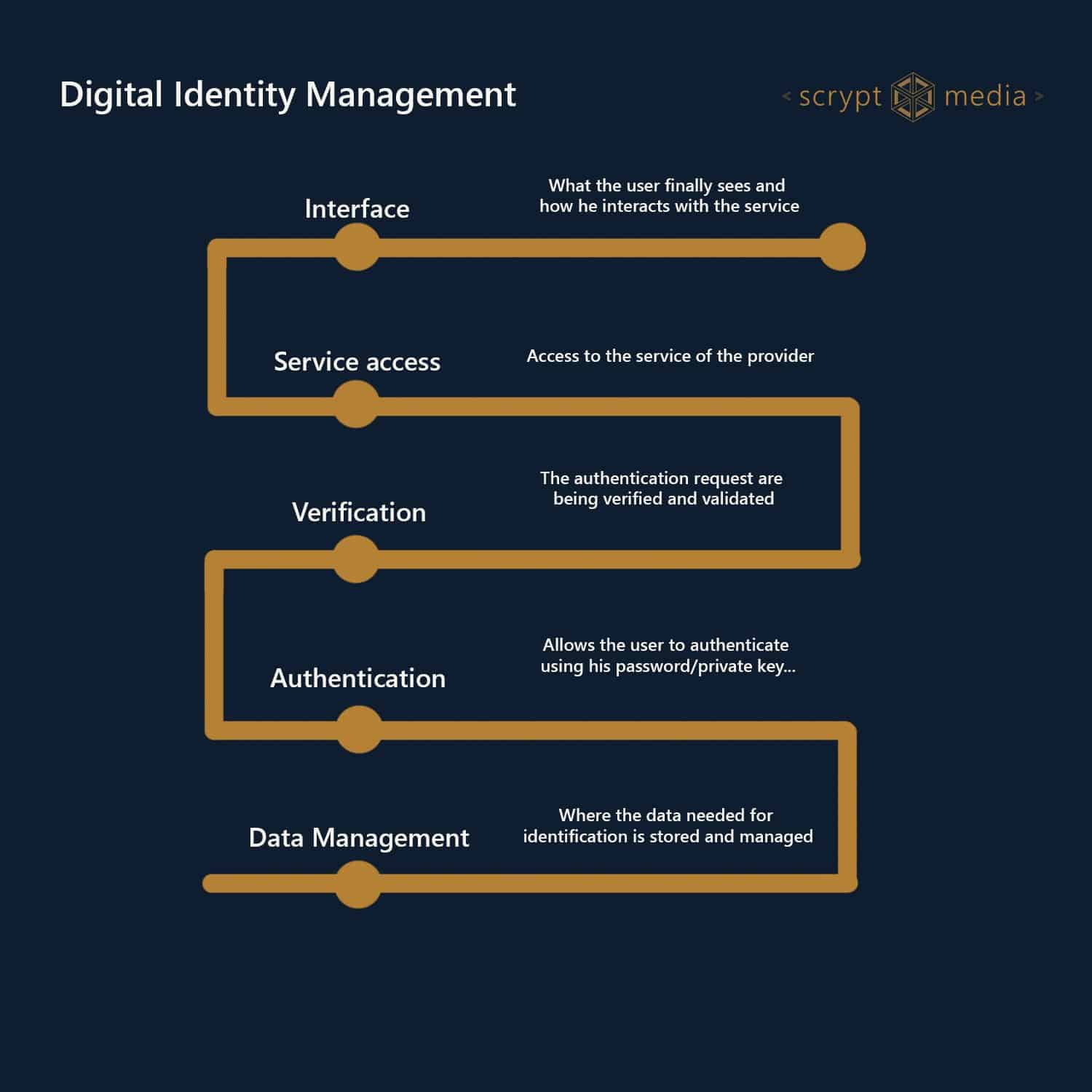
What Are Blockchain Identity Verification Tools?
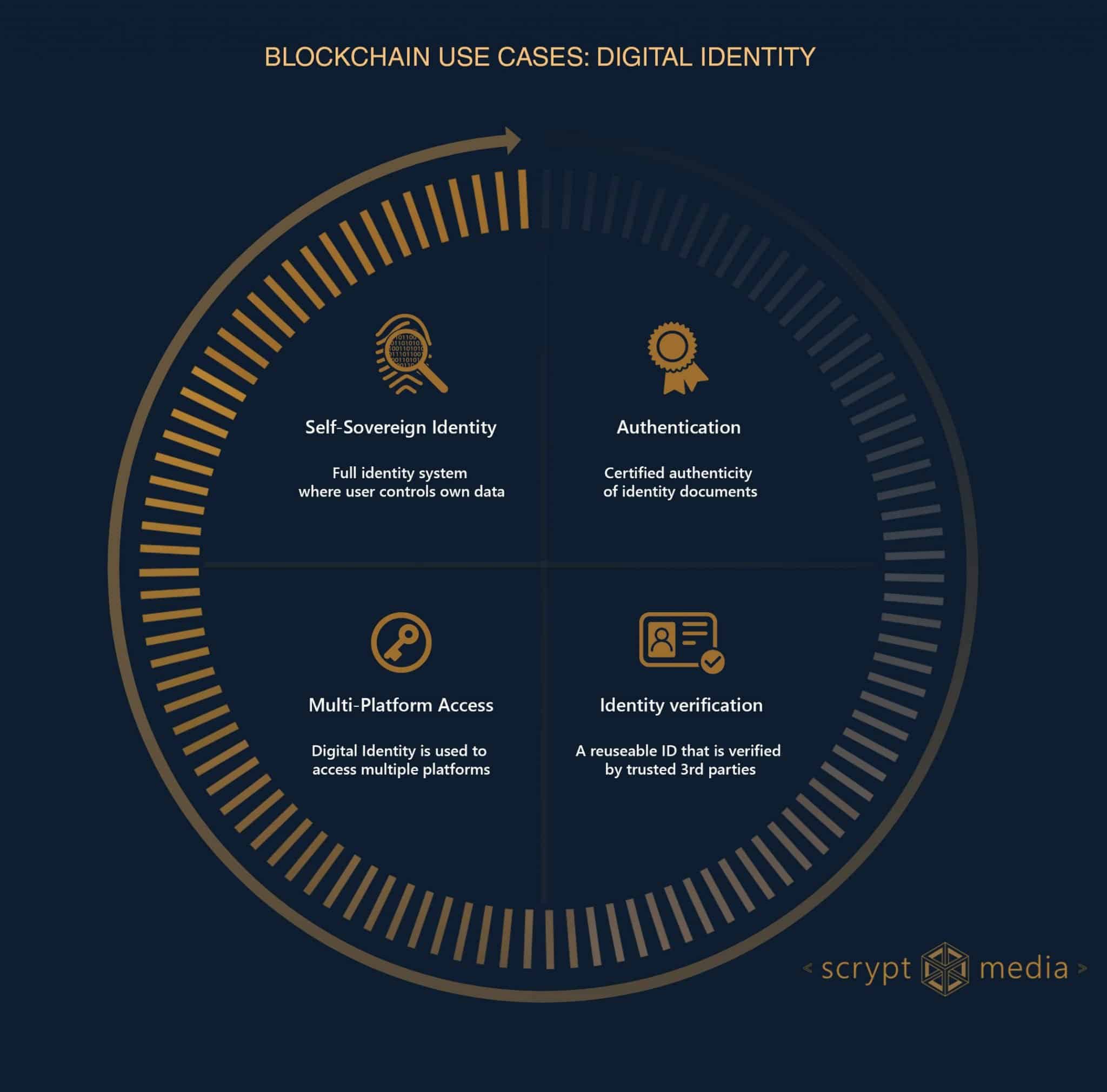
Blockchain identity verification tools are decentralized systems that enable users to create, control, and verify tamper-proof digital identities. Unlike traditional centralized management—where third parties like banks or governments hold all data—these tools empower users through digital wallets. This shift is rooted in self-sovereign identity (SSI), moving from “trust in institutions” to “trust in cryptography.” As explained by experts, this foundational change enhances security and autonomy. Blockchain identity management and digital identity use cases highlight the growing adoption of these secure digital ID systems.
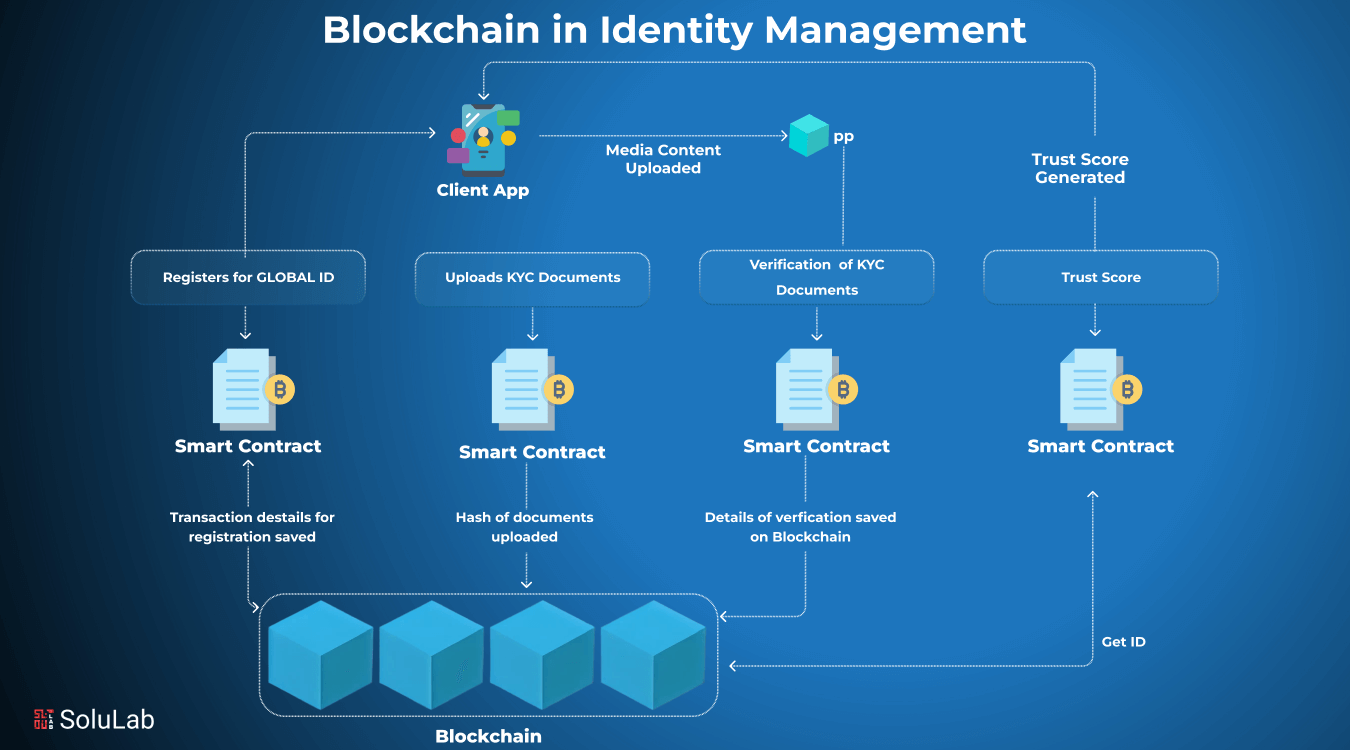
How Blockchain Technology Secures Digital Identity
Three core mechanisms make blockchain identity verification tools exceptionally secure:
1. Cryptographic Hashing
This converts identity data into fixed-size, unique strings. Each block contains a hash of the previous one, creating an unbreakable chain. Tampering changes the hash, making fraud detectable—like a unique fingerprint for data.
2. Decentralization
Instead of one vulnerable database, records are distributed across multiple nodes. This eliminates single points of failure; attackers can’t compromise the entire system by breaching one location. Network consensus validates all claims, as noted in studies.
3. Immutability
Once added, records cannot be altered or deleted, creating a permanent audit trail. This ensures accountability and non-repudiation, key for secure digital ID systems. Resources and whitepapers detail how immutability builds trust.
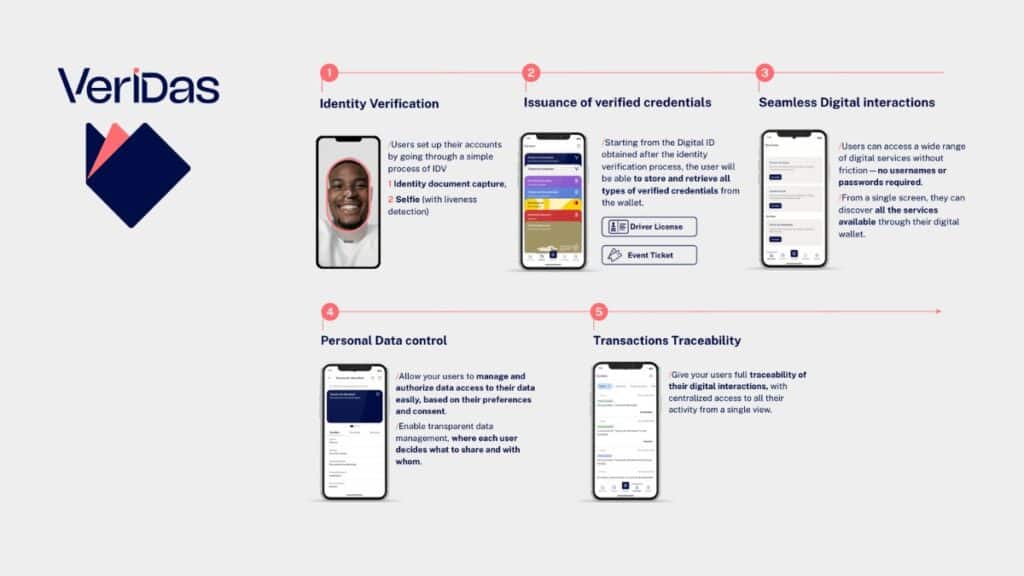
The Verification Process: How It Works in Practice
Here’s a step-by-step walkthrough:
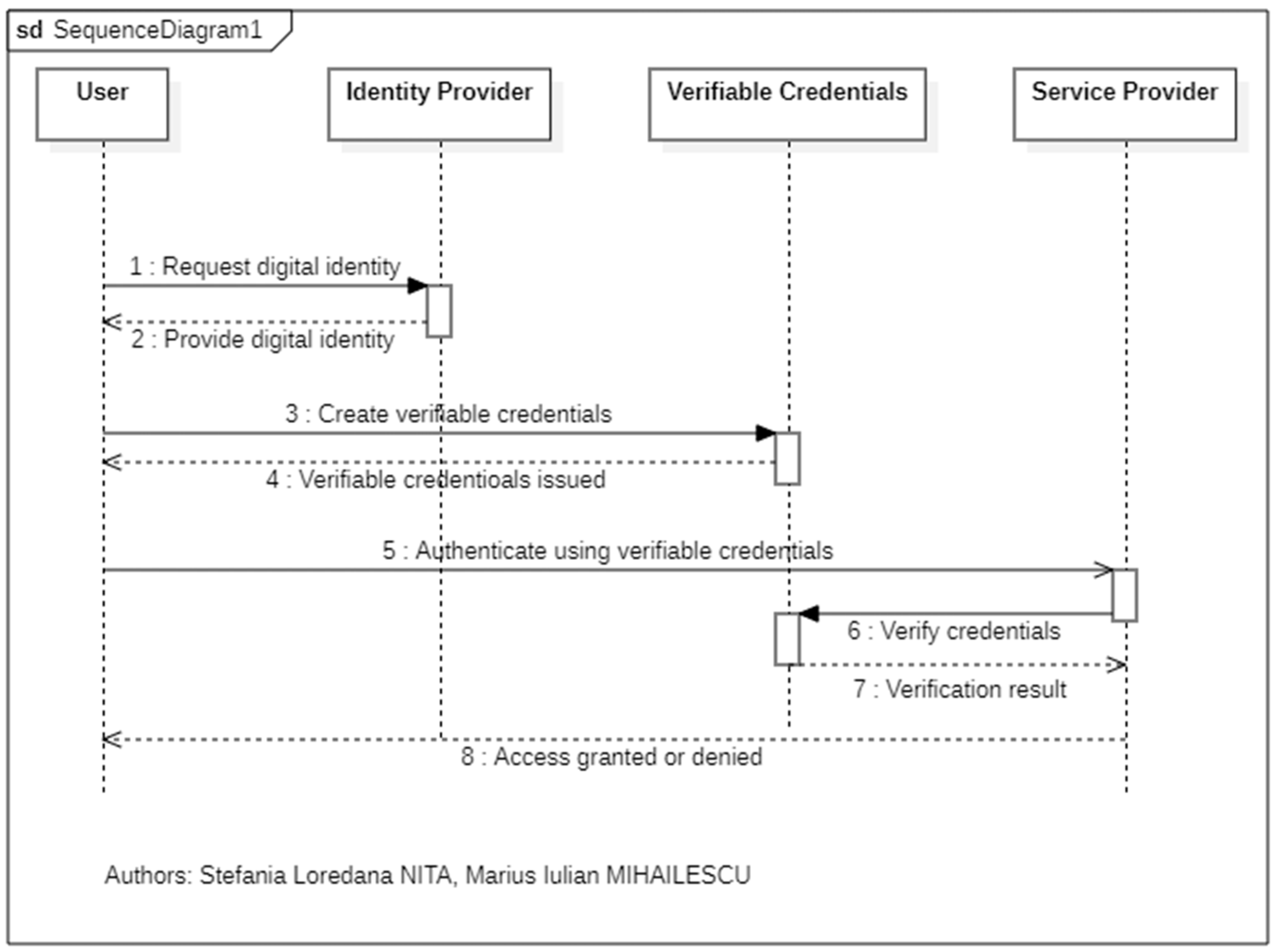
Step 1: Creating a Digital Wallet
Users create a secure wallet to store credentials, protected by cryptographic keys. The public key is shared, while the private key remains secret. Tip: For more on securing devices, see our guide on smartphone security.
Step 2: Issuing Verifiable Credentials
Trusted issuers (governments, universities) sign digitized documents with private keys, storing them in the user’s wallet—not on centralized servers.
Step 3: Presenting Proofs
Users present proofs via QR codes or data transfer, signing with their private key. Selective disclosure allows sharing only necessary info, like proving age >18 without a birthdate.
Step 4: Validator Confirmation
Network nodes confirm ownership through consensus, creating an immutable audit trail without single-entity control.
Decentralized Identifiers (DIDs) as the Standard
DIDs are globally unique identifiers anchored on blockchain, enabling portability across platforms. Analyses and case studies show how DIDs power blockchain identity verification tools.
Core Benefits: Why Blockchain Identity Verification Tools Matter
Benefit 1: Enhanced Security & Tamper-Proof Records
These tools eliminate single points of failure; breaches affect only portions of data. Cryptographic linkages make tampering evident, unlike centralized databases. Research confirms this superiority for secure digital ID systems.
Benefit 2: User Privacy Through Selective Disclosure
Users share only necessary info, minimizing exposure. For example, proving employment without salary details. Contrast with traditional systems where all info is revealed. Insights highlight this privacy tech. Learn more about protecting personal data online.
Benefit 3: Improved Efficiency & Interoperability
Seamless integration across platforms reduces friction. Smart contracts automate checks, like verifying bank accounts instantly. Guides discuss how blockchain identity verification tools cut costs.
Benefit 4: Proof of Existence & Digital Signatures
Hashing documents on blockchain creates permanent timestamps. Digital signatures ensure non-repudiation, enhancing authenticity. Studies underline this for secure digital ID systems.
Benefit 5: User Control & Autonomy
Users—not institutions—control data and access, shifting power dynamics. They can revoke access anytime, owning their identity. Examples show this empowerment.

Advanced Privacy Technologies Powering Blockchain Identity Systems
Zero-Knowledge Proofs (ZKPs): Proving Without Revealing
ZKPs are mathematical techniques that prove a claim is true without revealing underlying data. For instance, proving sufficient funds without showing balance. Experts call this revolutionary for privacy tech.
Embedded Encryption: Data Protection at Every Layer
Encrypted data is readable only with correct keys, even if intercepted. This layers security with blockchain. Analyses emphasize its role in secure digital ID systems.
Revocation Rights: User Control Over Credential Duration
Users can deactivate or expire credentials, preventing indefinite exposure. This gives ongoing control, as noted in resources.
Decentralized Storage & On-Device Processing
Data is distributed across nodes, and verification happens on-device, minimizing risks. This aligns with differential privacy principles. Research supports this privacy tech.
Consensus as Trust Without Compromise
Network agreement replaces institutional trust, maintaining autonomy while ensuring verification. Guides explain this balance.
The Role of AI in Enhancing Authenticity & Verification
While blockchain provides immutability, authenticity AI blockchain adds intelligent layers for comprehensive security.
AI as a Complement to Blockchain’s Cryptographic Foundation
AI ensures data authenticity, while blockchain ensures integrity. Together, they create robust blockchain identity verification tools. Discover more in our analysis on AI cyber defense.
Biometric Verification Enhanced by AI
AI-powered liveness detection confirms real persons, not deepfakes. Behavioral analysis detects anomalies, with biometric data stored encrypted. Case studies show this synergy.
Real-Time Fraud Detection & Risk Assessment
AI analyzes patterns, assigns risk scores, and flags fraud for review. Blockchain records these assessments immutably. Insights highlight this authenticity AI blockchain application.
Automated Verification & Streamlined Processes
AI automates checks using NLP and computer vision, reducing bottlenecks without sacrificing assurance. Examples demonstrate efficiency gains.
Future Potential: AI-Blockchain Synergy
Emerging possibilities include predictive analytics and continuous authentication. The convergence of authenticity AI blockchain creates intelligent, secure systems. Forecasts are optimistic.

Real-World Applications: Where Blockchain Identity Verification Tools Solve Actual Problems
Financial Services & Know Your Customer (KYC)
Banks use these tools for compliance, enabling one-time verification and smart contract automation. Use cases show reduced friction and costs.
Healthcare & Secure Medical Records
Patients own and control access to records via verifiable credentials. Selective disclosure allows sharing specific data without exposing history. Applications highlight privacy benefits.
International Travel & Tamper-Proof Passports
Digital passports resist forgery, with instant verification by immigration officials. Interoperability ensures global usability. Examples illustrate this for secure digital ID systems.
Voting & Verifiable Yet Private Elections
Blockchain ensures legitimacy while preserving ballot privacy using zero-knowledge proofs. Studies discuss this democratic solution.
Education & Verifiable Credentials
Universities issue blockchain-based diplomas; employers verify instantly without intermediaries. Cases show efficiency gains.
National Digital ID Programs
Governments implement portable, tamper-proof IDs for financial inclusion and security. Compliance strategies guide these large-scale deployments.
Current Tools & Technologies: Notable Platforms & Standards
Verifiable Credentials & Digital Wallets
Standardized formats for credentials include issuer info, claims, and cryptographic signatures. Digital wallets store and manage these, with DIDs enabling portability. Resources detail this for blockchain identity verification tools.
Decentralized Public Key Infrastructure (DPKI)
DPKI distributes key management across nodes, eliminating centralized authorities. It’s foundational for trustworthy systems. Guides explain its role.
Dock: A Platform for Blockchain Identity Management
Dock enables organizations to issue and verify credentials, demonstrating production-ready tools. Platform insights and verification details show practical use.
Standards & Interoperability Frameworks
Key standards like W3C Verifiable Credentials and DIDs ensure ecosystem compatibility. Frameworks support secure digital ID systems.
Real-World Example: DID-Based Attestations
A graduate shares a diploma credential via QR code; an employer verifies it instantly via blockchain consensus. Scenarios illustrate operational tools.

Overcoming Challenges: Adoption, Standards & the Road Ahead
Standardization & Ecosystem Maturity
Fragmentation across standards limits interoperability, but efforts around W3C and DIDs are progressing.
Regulatory Clarity & Compliance
Governments are developing frameworks; technical solutions address conflicts like GDPR’s “right to be forgotten.”
User Education & Trust Building
Education initiatives and intuitive wallets are making adoption easier as use cases become mainstream.
Scalability & Performance
Newer blockchains and layer-2 solutions improve throughput, overcoming engineering challenges.
Vision of the Future: Universal, User-Owned Identity
A world where everyone controls a portable, verifiable identity globally. This convergence of blockchain identity verification tools, privacy tech, and authenticity AI blockchain creates unprecedented trust. Explore the latest trends in cybersecurity threats to stay informed.

Frequently Asked Questions
What makes blockchain identity verification tools more secure than traditional methods?
They use decentralization, cryptographic hashing, and immutability to eliminate single points of failure and make tampering detectable, unlike centralized databases prone to breaches.
How do blockchain identity tools protect user privacy?
Through selective disclosure and zero-knowledge proofs, allowing users to prove claims without revealing sensitive data. Encryption and decentralized storage add layers of privacy tech.
Can blockchain identity systems work with existing AI technologies?
Yes, authenticity AI blockchain integrations enhance verification with biometric analysis and fraud detection, complementing blockchain’s security for smarter blockchain identity verification tools.
What are some real-world examples of blockchain identity verification in use?
Examples include KYC in banking, secure medical records in healthcare, digital passports for travel, and verifiable credentials in education—all detailed in case studies.
How can individuals get started with blockchain identity tools?
Explore digital wallet options and familiarize yourself with verifiable credentials. For everyday security, read our guide on cybersecurity tips.